The Importance of Protecting your Online Identity: 5 Tips to get started
Guest writer: Layal Khatib*
Security is a very important factor in every individual’s life. We secure our houses, finances, jewelry, cars, and other assets we find valuable, through setting up various defense techniques to counter potential robberies. Technology has taken over our daily activities, and has created additional assets that are now considered as valuable as owning a car or house. This includes digital data like emails, photos, banking accounts, etc. Similar to our physical assets, we have the responsibility of protecting our digital data (and which includes emails, bank details, photos, etc.) against potential security threats, identified in the online-world as cyber threats and crimes.
Securing your online presence does not necessarily require technical knowledge. Below are 5 tips to help you:
Choose strong passwords
Setting passwords is considered the first defense line of your online accounts, but also the easiest to crack if created poorly.
SplashData has published its annual list of the worst passwords of the year 2017 (created from more than 5 million passwords that were leaked by hackers). SplashData estimates almost 10% of people have used at least one of the 25 worst passwords on this year’s list, and nearly 3% of people have used the worst password, i.e. 123456.
When creating passwords, remember these 3 points:
- Simple passwords are easy to remember, but they’re also easy to guess by potential hackers, so it’s better to avoid them.
- Use strong passwords that are at least 8 characters long, and include numbers and special characters, such as using arabic characters (ex: أحببت حفلة فيروز في 5 حزيران@ بيروت). Having strong and long passwords also protects you from a brute force attack, which is a trial-and-error method used by hackers to generate all possible string combinations until it’s cracked.
- Do not use the same password across applications and websites. Making sure your passwords are unique offers a greater level of protection for your overall cyber presence.
Don’t click on malicious links!
Unfortunately protecting your account with a strong password may not deter the persistent hacker.
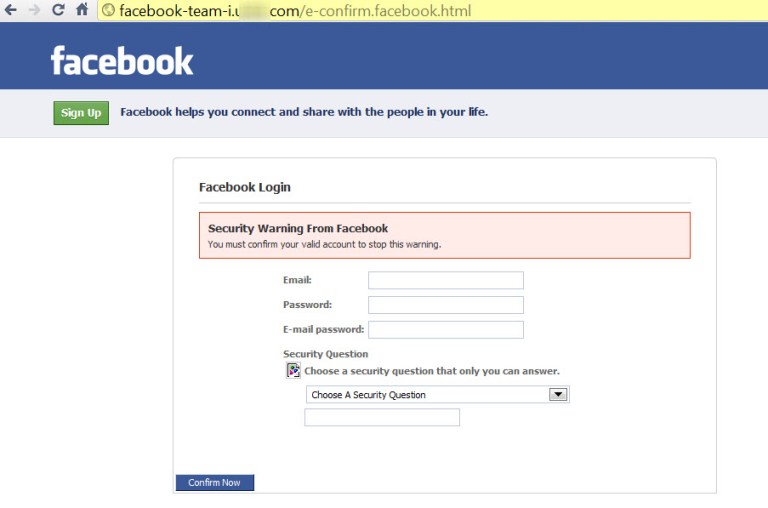
Hackers may pursue your password by phishing. For example, they may create a page that looks exactly like Facebook’s login page, send it to you in a random message asking to confirm your identity, or even invite you to follow a link to see a hilarious video, in the hopes of directing you to a malicious link.
After you enter your strong Facebook password your account will be hacked.
Furthermore, hackers may even block your access to your own device system by tricking you into downloading a ransomware application disguised as a trusted application.
Remember the below:
- Always check the links you get before giving away critical information, or downloading unknown apps.
- Keep in mind that a company would never send you offers or ads that are not linked to their websites. For example, Samsung would never give away 10 mobile phones through sending a whatsapp message.
Love your 2-Factor authentication
Technology is changing on a daily basis and hackers are becoming better at adapting to it too. Many major websites/apps now offer an extra defense to strengthening the protection of your accounts, such as 2-factor authentication.
If the latter is enabled, it can send a request to insert your password to let you proceed with using the website, or request to enter a pin code that is sent to your mobile in an SMS. This will ensure the security of your account, and if compromised, it will keep it safe.
Read about how to enable 2-factor authentication at Google, Facebook and Twitter.
Avoid Social Media oversharing
Another way hackers might try to get access to your account is by resetting your password. Many online services provide ways other than emails to validate the ownership of an account. One of these ways is setting a secret question/answer. You may think that writing your childhood pet’s name is a good option for such questions, until you share a #throwback picture on your Instagram page of your dog, “Max”.
Oversharing your whereabouts and assets on social media also compromises, at many levels, your physical security, not just your virtual one. When reality TV celebrity, Kim Kardashian, was robbed in Paris back in 2016, the robbers admitted that they used her social media posts to track her location, after they knew that she was wearing her 4.5 million dollar wedding ring (read here how they planned the whole robbery).
Always be careful what you share online.
Limit your activity on public networks or use VPN/Tor
One of the easiest way to allow the hacking of your account is connecting to the open access wifi of a public space. If you’re connected to a wifi network with a hacker, chances are high they’re able to watch what you’re doing.
When working from a café for example, remember to: Never share any sensitive information while using an open-access internet. If you really must use one, use a Virtual Private Network (VPN) which will encrypt and anonymise your traffic. Such networks are easy to set on your laptops and mobile phones. (Read more about it: Best VPN Services for 2018 by PCMag)
*Layal Khatib is a mother of two, and a FOSS enthusiast from Lebanon. She is the lead developer at SHFRA studio and a consultant to Lebanon Support’s programme, Daleel Madani, mainly responsible for the technical support and development of the website. After Layal assures that her work deadlines are met, and her two little girls are asleep, she dedicates what is left from her quality time to play some classic guitar.